
Network & Security
Our company specializes in providing top-notch Security Operation Center services. With the ever-increasing threat landscape, it has become crucial for businesses to safeguard their sensitive data and prevent unauthorized access. Our team of skilled professionals is dedicated to ensuring the utmost security of our clients' networks and systems. We employ advanced technologies and industry best practices to assess vulnerabilities, detect potential threats, and implement robust security measures. From setting up firewalls and intrusion detection systems to conducting regular security audits, we offer comprehensive security solutions tailored to meet the unique needs of each client. With our expertise and reliable support, businesses can have peace of mind knowing that their networks and systems are protected against cyberattacks and data breaches.
The Unified Security Platform

Comprehensive support for detection, analysis, and response to known, unknown, and suspected threats
SOC (Security Operation Center)
Build with SIEM as the core, targeting both external and internal threats (through UEBA)
Detection: Threat detection is carried out through SIEM's rule engine (constructed threat detection model), which detects threats in real-time and associates them with the Threat Intelligence Platform (TIP) to improve alarm accuracy.
Analysis: By analyzing security events from the network dimension (NTA) and endpoint dimension (EDR), identify and track suspicious attacks and abnormal behavior;
Response: Driven by SOAR, combined with blocking devices/systems (anti D/boundary firewall/WAF/AD/fortress machine/others), respond to discovered security events (IP blocking/account locking/others)
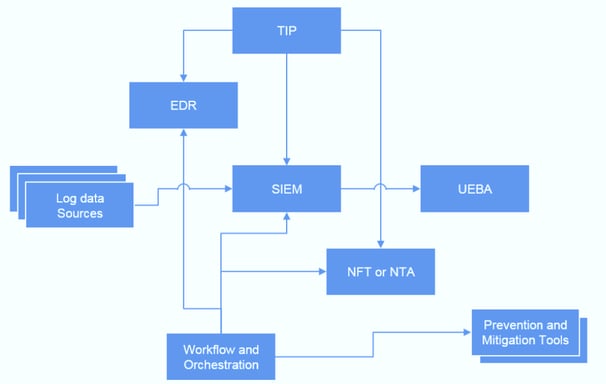
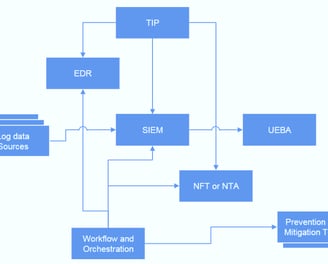
SIEM: Security Information and Event Management
UEBA: User and Entity Behaviour Analytics
NFT/NTA: Network Forensic Tools/Network Traffic Analysis
Workflow and Orchestration: Security Orchestration Automation and Response
TIP: Threat Intelligence Platform
EDR: Endpoint Detection and Response








Collect, manage, retrieve, and correlate log data of various production environments, including but not limited to security devices, network devices, middleware, operating systems, databases, application layers, and other logs.
Combined with network layer and endpoint layer events to analyze abnormal behavior, trace the source of the attack chain from the timeline dimension, and discover the horizontal scaling behavior through correlation analysis.
Data Collection, management, retrieval
Investigation and Forensics
Threat Detection, analysis and response
Provides common event processing and detection rules such as web security and host security, and correlates asset data, vulnerability data, and intelligence data to detect, block, and automatically respond to threat events.
Conduct regular audits of abnormal and illegal operations of intranet users, and output compliance audit reports.
Compliance Audits
Product advantages

High-performance self-developed search engine
The bottom layer adopts a search and analysis engine with independent intellectual property rights, which is secure and controllable, and processes hundreds of new logs every day.
Flexible correlation analysis
Self-developed SPL (Search Processing Language) search processing language, supports hundreds of functions, instructions, through different time periods, different types of data to compare and correlate analysis, find new threats and anomalies.
Powerful real-time computing power
Provides a real-time streaming computing framework that supports real-time data analysis and computation based on different security scenarios (aggregation, association, etc.), and supports distributed deployment.
Machine learning capabilities
Dozens of mainstream machine learning algorithms in five categories, including built-in regression, preprocessing, time prediction, classification, and clustering, are used to detect internal user and entity anomalies and achieve in-depth intelligent security analysis.
Location
3601, 6F Tung Hip Commercial Building, 244-248 Des Voeux Road Central,Sheung Wan, HK.
Hours
Monday-Friday 9:00-18:00
Saturday - Sunday Closed
Contacts
+00852-68527937;0086-13601397676
service@cwboan.com
